Safeguarding Essentials Resources - E-safety News and Information Widget
E-safety News and Information Widget
|
Add the E-safety News and Information Widget to Your School Website Schools can now reach their whole school community with this free resource from Safeguarding Essentials. By adding the E-safety News & Information Widget to your school website, teachers, parents, pupils and school governors will be able to see the latest news, articles, definitions and up-to-date information about e-safety issues every time they visit the school website. The E-safety News and Information Widget is a simple service available to all Safeguarding Essentials members including Free membership. By copying and pasting a few simple lines of code you can add the widget onto a page on your school's website. The image to the left demonstrates how this would appear. Every time we have an e-safety update, you will too. Log in to your Safeguarding Essentials dashboard for further instructions and the code for adding the widget, or join now if you are not already a member. If you are from a company or organisation which is not a school, but would like to add the widget to your website, please get in touch – we would be happy to hear from you. Simply email your details to info@kodoeducation.com |

This document is an Acceptable Usage Policy (AUP) suitable for primary school pupils and parents. Young people need to understand the basic rules for using ICT in school and for school purposes, which is where the AUP comes in. The document can be used as is, or it can be adapted for your own use. It covers the use of school IT systems, email and social media, privacy, Data Protection, use of images and more.

Every school needs to have an Acceptable Usage Policy (AUP) for their staff and other stakeholders. This document is suitable for use by staff, support staff, governors, visitors, wider stakeholders with access and external contractors. It encourages responsibility for e-safety and clearly outlines how ICT can be used safely in and out of school.

These E-safety Support resources offer simple questionnaires that you can use with your key stage 1 and key stage 2 pupils to learn how they are using the Internet and to gauge their understanding of appropriate use. Both questionnaires are in multiple choice format, with more detailed questions for the older students. You can use the results to assess the e-safety learning requirements in your class and identify areas where they are potentially at risk.

This document contains a number of questions that can be used as part of an audit or survey to get an idea of the current levels of parental awareness when it comes to e-safety. The result will help schools to plan their e-safety content and strategy. You can use the survey as it is, or cut and paste to create a shorter version to suit your requirement. You can then send it by post or by email to parents, or ask the questions face-to-face at presentations.
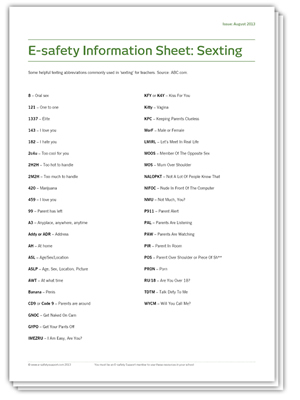
It seems that there is a whole new language developing in the digital landscape - LOL!. But while many are playful and literal abbreviations, some are more potent.
To help make parents (and teachers) aware of some of the sexting abbreviations, we have compiled a short glossary. This is by no means exhaustive, but will help to educate parents about this new form of communication.

Providing a presentation to parents on e-safety, as a standalone event or as part of wider activities, is a great way to raise awareness, encourage discussion and promote good practice. However, it can take a lot of work to organise. That's why we have created this PowerPoint for you. It covers all the areas you'll want to cover, but can easily be adapted for your individual needs. You can also make it available online for parents to recap or who may have missed the event. The PowerPoint contains links to video in the notes sections of relevant slides.

This e-safety policy template provides a useful starting point for your e-safety strategy in school. The document has been saved in Word, meaning that it is fully editable by the user. You can cut, copy and paste your own requirements into the template, or choose to leave it largely as it stands, if it is suitable for your school. The policy includes a number of clear, easy to follow statements, as well as substantial guidance and support for everybody in the school.

This guidance document is for teachers to help them engage parents with e-safety. The document has been written by an experienced ICT teacher who has worked successfully with parents and schools on e-safety. The guidance will help you plan content and activities for parents around e-safety and make sure you get maximum impact and engagement. It includes advice and tips on planning your content and activities, delivering them and following up.

A key element of e-safety provision in schools is the clear and effective use of reporting procedures. Ofsted will expect all staff and students to know how to report e-safety incidents, and how to recognise when an incident has occurred. The guidance document starts from a common sense approach which is easy for all schools to implement, and helps teaching staff understand what constitutes illegal or inappropriate content. They are then given instructions as to the appropriate response and reporting mechanism. Recommendations are made as to best practice and the protection of children and staff in case of an e-safety incident.

What makes a password strong? The key to creating a strong password is to understand how your password might be stolen, hacked or guessed. This guidance document gives teaching staff an overview of how this is done, and how you can protect yourself. The information can easily be edited and reproduced for the benefit of students or younger pupils. The guidance includes tips for strong passwords, what to avoid doing when you create a password, and useful links for secure password generation, remembering passwords, and creating an encrypted text file to store your passwords. Password security is a key issue in e-safety for everybody, so it is vital that teaching staff understand this and are able to prove to Ofsted that password security is taken seriously in school

The Parent Pack of resources includes factsheets, an audit questionnaire, a PowerPoint presentation and guidance for teachers. This document explains how each of these resources can be used by teachers and e-safety co-ordinators to improve communications between parents and schools.

A useful assembly for an e-safety recap or introduction, this assembly raises key online safety issues such as cyber bullying, security, inappropriate content, trolls, plagiarism and bogus websites. The teacher takes the children through each issue and helps them to understand how they can avoid it, or deal with it. The assembly includes a script for the teacher, and a PowerPoint presentation for the children.

In this assembly, children at key stage 2 are encouraged to think critically about information they source online. Using an excellent spoof website about the endangered “tree octopus”, the teacher demonstrates how young people can tell that information is incorrect.
They are also introduced to the idea that Wikipedia isn’t always the best source of information, and that communications such as chain emails or texts should be ignored. The assembly closes with a number of top tips for helping children to decide if a website is genuine or not. This assembly includes a PowerPoint presentation for displaying at the assembly and a script for the teacher.

This assembly helps young people to understand the risks and consequences of illegally listening to music online, of downloading music illegally and copying downloaded files. It also touches upon the illegality of uploading copyrighted content. The teacher explains the risks, the possible consequences, and how to avoid illegal downloads. The assembly comes with a script for the teacher and a PowerPoint presentation to use with the children.

Young people spend increasing amounts of time online, as well as watching TV and instead of playing outdoors. This assembly raises the issue of being addicted to using the Internet, whether it is for social networking, gaming or research. The teacher explores possible consequences of Internet addiction, including social and health impacts, and offers advice on reducing time spent online. The assembly includes a PowerPoint and a script for the teacher.

Many younger children are exposed to film, TV and gaming content that is certified as being suitable for much older young people. Younger boys in particular will be keen to play online or console games that have a 15 or even 18 certificate. These games will have violent or sexual content that is entirely inappropriate for younger children. In this assembly children learn about the BBFC and PEGI classifications, why they exist, and how they work. They also consider the implications of watching films or TV shows that have been illegally downloaded. The assembly includes a PowerPoint and a script for the teacher to read from, or use as a starting point.

By key stage 2, pupils should be well aware of the risks of stranger danger online. This assembly reinforces understanding and awareness about grooming and inappropriate contact. The assembly concludes with a fun "Who wants to be a Millionaire" style quiz.
-
 Teacher Script for Stranger Danger
Teacher Script for Stranger Danger
-
 PowerPoint Presentation for Stranger Danger
PowerPoint Presentation for Stranger Danger
-
 PowerPoint Presentation for Stranger Danger - Part 1
PowerPoint Presentation for Stranger Danger - Part 1

This primary assembly resource, which engages with the PSHE curriculum, allows a KS2 primary teacher to focus on developing children’s awareness and understanding of cyber bullying and the importance of staying safe when using technology to communicate.
The assembly aims to provide advice and explanation about cyber bullying without frightening primary-age children. The assembly then develops the primary children’s awareness of the issue by explaining how varying forms of cyber bullying occurs through different technologies such as mobile phones, social-networking and online gaming.
Primary school teachers will be able to use this idea for an assembly to give the children the information, awareness and capability to know if someone is cyber bullying them or if a friend is being targeted. Through the assembly, the children will know how to react to cyber bullying and the appropriate actions to take.

This assembly can be used to support the school’s safeguarding work and to ensure that pupils feel confident to speak out if they have worries or concerns and know who to approach.
The aim of this key stage 1 and 2 assembly is to ensure pupils feel safe and know what to do if/when they do not.
-
 Teacher Script for Safeguarding Assembly
Teacher Script for Safeguarding Assembly
-
 PowerPoint Presentation for Safeguarding Assembly
PowerPoint Presentation for Safeguarding Assembly

This assembly provides pupils with an understanding of what drugs are (including alcohol and tobacco) and the physical consequences of taking controlled substances.
Pupils are encouraged to consider things that make them feel good, to help them compare the physical feelings against the negative effects of drugs.
-
 Teacher Script for Drugs Assembly
Teacher Script for Drugs Assembly
-
 PowerPoint Presentation for Drugs Assembly
PowerPoint Presentation for Drugs Assembly

This key stage 1/2 assembly is designed to help younger pupils understand that not all illnesses have physical symptoms. It introduces the idea of mental well-being and discusses ways to help maintain good mental health.
-
 Teacher Script for Mental Well-being Assembly
Teacher Script for Mental Well-being Assembly
-
 PowerPoint Presentation for Mental Well-being Assembly
PowerPoint Presentation for Mental Well-being Assembly

This key stage 2 assembly is designed to help pupils develop an awareness of FGM, what it is, where and why it happens as well as knowledge of where to seek help and advice.
-
 Teacher Script for FGM Assembly
Teacher Script for FGM Assembly
-
 PowerPoint Presentation for FGM Assembly
PowerPoint Presentation for FGM Assembly

This assembly will help pupils develop their awareness of what alcohol is. They will also learn about the rules about young people and alcohol and the physical effects of drinking alcohol.
The assembly includes some open questions to help engage the pupils in the assembly.
-
 Teacher Script for Alcohol Assembly
Teacher Script for Alcohol Assembly
-
 PowerPoint Presentation for Alcohol Assembly
PowerPoint Presentation for Alcohol Assembly

In this assembly designed for key stage 2, pupils are given an understanding about the risks of sharing information via the Internet (primarily images). They will also be introduced to why it’s not always appropriate to share and learn about privacy settings.
-
 Teacher Script for Sexting Assembly KS2
Teacher Script for Sexting Assembly KS2
-
 PowerPoint Presentation for Sexting Assembly KS2
PowerPoint Presentation for Sexting Assembly KS2

This key stage 1, primary circle time resource allows teachers to focus on developing children’s awareness and knowledge of staying safe whilst using the Internet. The resource engages with the primary PSHE curriculum and teaches young children that there are adults, using the Internet, who pretend to be children to form inappropriate relationships with them.
Through engaging exercises, the circle time activity offers advice and explanation about staying safe whilst using the Internet without frightening primary-age children. The activity concludes with the children developing their own set of rules and turning them into a poster. This activity reinforces what they have learnt and allows them to recall the rules of safe Internet use when they are using the Internet at home.

This key stage 2 lesson plan is underpinned by teaching and learning activities related to the three areas of risk in e-safety: content, contact and conduct. Through discussion and activities, teachers explore the range of ways in which content can be shared via the Internet, specifically mobile devices. The lesson helps children understand how Wi-Fi and 3G- or 4G-enabled devices offer a range of ways to communicate with others and receive communications, and identifies the advantages, disadvantages and dangers associated with online communications while suggesting ways in which risks can be minimised.
The lesson also covers what is meant by communications ‘going viral’ and how this applies to text or multimedia messaging.

Research shows that many children play console or online games and watch films that are classified as being suitable for older users. This lesson is designed to help children make more informed decisions about the games they play or the movies they watch. What are classifications and how do they work? What is the difference between movie and gaming classification systems? The lesson also tackles the issue of how to assess the risk of watching unrated video online, and how children can deal with something they have seen that upset them.
The key stage 2 lesson includes links to relevant multimedia online, so will work best if you are able to use a whiteboard or projector.

The ability to evaluate websites for their validity is highly important as children increasingly turn to online content for research purposes. In this lesson children understand that online content can be unreliable, and it can be used to pass on fiction and myths. The children use an example of a spoof website to help them identify suspicious information. Unreliable online information can compromise their ability to learn and understand the world, so it is important that they learn how to spot it, and check data. The lesson also explores how to spot scams or fraud, and what to look out for.
Included in this KS2 resource are a PowerPoint presentation and a website evaluation form template to be used by the children when examining online sources of information.

Anyone who has seen children merrily copying and pasting images from the Internet into their homework or searching Wikipedia for information on a topic, knows that knowledge and understanding of the concept of copyright needs to be absorbed very early on, to prevent plagiarism incidents at secondary school or university. As well as understanding that information online is not always correct, children also need to know that websites and the content of websites are protected by copyright, in just the same way as books are. Young people need to understand that taking information from the Internet can have legal implications and puts individuals at risk of breaking the law.
This KS2 lesson could form the basis for the next lesson, where children share their learning about e-safety and issues related to use of online content with a wider audience. It includes links to useful websites that can help with this potentially complex issue, a PowerPoint presentation and resource sheet.

This lesson gives key stage 2 pupils an opportunity to collate all their online safety learning from previous lessons, all their e-safety knowledge, and create a display, presentation or factsheet summarising their knowledge for the rest of the school and potentially their parents too.
You could use the key messages from this session to create an e-safety charter, which feeds into the schools e-safety policy, which is “good or outstanding” practice according to Ofsted.

In this assembly designed for key stage 1 and 2, children will learn to judge what kind of physical contact is acceptable and comfortable or unacceptable and uncomfortable. They will also learn how to respond (including who to tell and how to tell them).
-
 Teacher Guide for Abuse Lesson
Teacher Guide for Abuse Lesson
-
 Class Presentation for Abuse Lesson
Class Presentation for Abuse Lesson

Ofsted have identified the lack of effective procedures for securing data in school as a weak point. As part of a school's e-safety strategy, it is vital that the large amount of personal and sensitive data that a school is likely to be responsible for is properly secured and treated. This briefing document gives teachers an overview of the key issues, including defining personal data, the Data Protection Principles, the difference between personal and private data, and what to include in a fair processing and privacy policy. The guidance also offers advice about handling personal data on portable devices and remote access, as well as encryption and correct disposal of personal data. Best practice tips are also included.

This template document in Word allows you to create your own social media policy for teachers. Simply add your school name, the date, then cut and paste your own content into the document, or use it largely as it stands. The document includes guidance and policy notes, and is a useful reinforcement for a schools' e-safety policy, specifically about the use of social media.

Digital literacy is not simply maintaining and developing a familiarity with computers, the internet and the possibilities afforded by incorporating ICT – it is more about future proofing learning, keeping teaching accessible and relevant to pupils, and extending and embedding key skills and concepts into pupils lives – both in and out of school.
In the What Every Teacher Needs to Know About Digital Literacy report, find out how to use ICT, the internet and digital devices to enhance learning and also prepare students for a digital future.

This Acceptable Usage Policy (AUP) is suitable for secondary pupils and parents. It covers important e-safety topics and fosters an understanding of the key issues surrounding usage of ICT and the Internet in and out of school. These include use of school IT systems, email and social media, privacy, Data Protection, use of images and more. The policy can be used as it is, or adapted for your particular requirements. It encourages responsibility from parents as well as students.

As pupils become more advanced users of the Internet, it is important to understand how they interact with other users and also how they perceive the online actions of themselves and their peers. The E-safety Support audit for key stage 3 and key stage 4 offers a detailed self-assessment for pupils, which will help you to understand not only the actions of your pupils but also the thoughts and behaviours associated with their Internet use.

Ensuring that the whole school is familiar with e-safety issues extends from the students to the staff, the senior leadership team and through to the governors. These E-safety Support audit surveys are designed to help ensure that your school is making everyone aware of their responsibilities in delivering a comprehensive e-safety strategy. The multiple choice questionnaires will monitor the awareness of e-safety issues and the schools’ policy in practice among this key stakeholder group.

Sexting is when sexually explicit text messages are sent from mobile phones or tablets. These could be text or image based. This assembly clarifies what sexting is, what the risks are, and what the law says about sexting. It uses two case studies that have been in the press to illustrate key points and dangers. The assembly includes a teacher script and a PowerPoint for display.

This important and relevant secondary assembly resource allows key stage 3 and 4 teachers to raise their students’ awareness and understanding of the issue of ‘Digital Media Piracy’ and supports the delivery of ICT, PSHE and citizenship.
The assembly plan begins by testing the students’ knowledge of the subject by asking them various questions associated with ‘Digital Media Piracy’. This is to raise their awareness that some of the practices they may carry out such as copying music or films for friends may be breaking the law without them realising it.
The assembly then turns it’s attention to the argument that pirating digital media is impacting the creation of new music and other media. Various facts are presented for discussion with the students and although both sides to the argument is offered, great care has been taken not to reduce the seriousness of committing digital piracy, which obviously remains illegal.

This stimulating secondary assembly resource allows secondary school teachers to use the assembly to highlight the dangers of spyware and raises the students’ awareness and understanding of this important subject. The assembly commences by highlighting that spyware is one of the biggest problems on the Internet and is, and will continue to be, a serious threat to the security of both personal and business data.
The students are asked to attempt to define what spyware is and then invited to provide explanations as to why anyone would want to create spyware. The assembly also draws the students attention to the fact that once the information has been gathered it is then free to be passed on with the potential of getting into the wrong hands and leading to fraud or identity theft.
Students learn how to protect their computers against infection from spyware by emphasizing that the best approach is to prevent spyware getting onto machines in the first place. The assembly concludes by emphasizing that by preventing spyware infection the students are ensuring that both their data and their computer will be much safer and secure.

This engaging secondary assembly resource allows secondary school teachers to raise the students’ awareness and understanding of the issue of Malware. The associated presentation starts by asking the students to provide their own definition of what Malware is, followed by an official definition.
Students take part in a quiz where definitions of different categories are provided and the students guess what type of malware is being described.
After the quiz, the presentation looks at some of the methods that malware writers use to infect peoples’ computers with their malicious code. The assembly then turns to the best ways to stop malware getting into the students’ computers. It informs them that prevention is better than cure and offers various suggestions to prevent infection such.

This fascinating secondary assembly resource gives secondary school teachers the opportunity to use the assembly to explain what is meant by the term ‘digital footprint’ and raises the students’ awareness and understanding of why it is important.
The assembly commences by giving the students an opportunity to explain what they think is meant by the phrase ‘digital footprint’. The assembly then explains that whenever we subscribe or sign up to a website, we are encouraged to post aspects of our lives online and that worryingly, most of this information is freely available for anyone to view and collect.
The presentation then moves onto describe what methods the students can deploy to uncover their own ‘digital footprint’, such as simply searching for their own name on Google and other search engines. The assembly then shift to the reasons why we should take care with what we contribute to our ‘digital footprint’ highlighting issues such as the increasing number of employers who are searching the Internet for the ‘digital footprints’ of potential job applicants. The assembly concludes by describing some of the things students can do to capitalise on their ‘digital footprint’ by showcasing work that demonstrates their skills, experience and knowledge.

This stimulating secondary assembly resource allows KS3 and KS4 secondary teachers to focus on developing students awareness and understanding of cyber bullying as part of the PSHE/Citizenship curriculum. This assembly plan sets out to provide advice, awareness and explanation about what cyber bullying is and the many forms it can take.
The students are then informed about the people that may get involved in cyber bullying such as the person who is retaliating on behalf of a wronged friend, the bully who wants to exert his/her authority, those who just do it for entertainment and the ones who cyber bully just because they can and they want to appear tough online.
This cyber bullying assembly plan offers secondary school teachers the opportunity to give the students the information, awareness and knowledge to know if someone is trying to cyber bullying them or if a friend is being targeted. Through the assembly, the students will learn how to react to cyber bullying and where to find information on what actions they should take to stop it.

This excellent secondary assembly resource allows secondary teachers to raise their students’ awareness and understanding of the phenomena of internet trends, which became popular due to their proliferation over social networks.
Using the associated presentation, teachers can use the assembly to talk to the students about both the positive outcomes that can be achieved by online trends and also the risks that can become part of certain internet crazes.
The presentation also talks about the peer pressure associated with participating in crazes and the potential for bullying.
This assembly replaces the previous assembly on Neknomination - this can still be downloaded for reference

The main focus of this secondary assembly is to encourage pupils to think critically when using the internet and consider that bias and opinion is an intrinsic part of the internet.
It will cover a number of key areas:
• Is everything on the internet true?
• How do people use the internet to attract attention to their cause
• Tips on how to evaluate web information
-
 Teacher Script for Extremism
Teacher Script for Extremism
-
 PowerPoint Presentation for Extremism
PowerPoint Presentation for Extremism

This assembly designed for KS3 and KS4 pupils takes a look at the history of alcohol, some of the statistics surrounding the use of alcohol, the law and the effects of alcohol abuse.
The assembly also gives pupils the opportunity to think about why they may drink alcohol and the pressures they may face to drink underage.
-
 Teacher Script for Alcohol Secondary Assembly
Teacher Script for Alcohol Secondary Assembly
-
 PowerPoint Presentation for Alcohol Secondary Assembly
PowerPoint Presentation for Alcohol Secondary Assembly

Use this assembly to help students gain a greater understanding of the effects of drugs on individuals and society.
Students will be encouraged to think about how drugs are glamorised, and what the reality is. They will also look at how the use of drugs can affect those around us.
-
 Teacher Script for Drugs Secondary Assembly
Teacher Script for Drugs Secondary Assembly
-
 PowerPoint Presentation for Drugs Secondary Assembly
PowerPoint Presentation for Drugs Secondary Assembly

This assembly will help key stage 3 and 4 pupils build on their understanding of mental health issues.
The assembly includes causes, statistics and ways to promote positive mental well-being.
-
 Teacher Script for Mental Well-being Secondary Assembly
Teacher Script for Mental Well-being Secondary Assembly
-
 PowerPoint Presentation for Mental Well-being Secondary Assembly
PowerPoint Presentation for Mental Well-being Secondary Assembly

In this assembly designed for key stage 3 pupils, students will develop an awareness of the different types of abuse and how to identify if abuse is taking place.
During the assembly, different scenarios are presented to help young people consider the possibility of abuse taking place in particular situations. They are also guided towards support available if they have any concerns.
-
 Teacher Script for Abuse Assembly (KS3)
Teacher Script for Abuse Assembly (KS3)
-
 PowerPoint Presentation for Abuse KS3 Assembly
PowerPoint Presentation for Abuse KS3 Assembly

The aim of this assembly is to introduce students to the issue of domestic abuse, as well as giving students strategies for identifying potential relationships suffering from abuse.
The theme of this assembly has been chosen given the age of the learners and the likelihood that many of them will be in relationships themselves. Content and statistics are age-appropriate and highlight an important area for them, whilst pointing out the impact domestic abuse can have on younger learners within school.
-
 Teacher Script for Abuse Assembly (KS4)
Teacher Script for Abuse Assembly (KS4)
-
 PowerPoint Presentation for Abuse KS4 Assembly
PowerPoint Presentation for Abuse KS4 Assembly

This assembly can be used in the context of both PSHE or citizenship education. Throughout the assembly, pupils will build an awareness of FGM, what it is, where and why it happens as well as the health effects and knowledge of where to seek help and advice.
-
 Teacher Script for FGM Secondary Assembly
Teacher Script for FGM Secondary Assembly
-
 PowerPoint Presentation for FGM Secondary Assembly
PowerPoint Presentation for FGM Secondary Assembly

Some of our assemblies are replaced over time, however, you may still find the material they contain useful.
The assemblies that are contained in this section are no longer updated, but can still be downloaded.
Archive Assembly: 1 Neknominate
-
 ARCHIVE - Teacher Script for Neknomination
ARCHIVE - Teacher Script for Neknomination
-
 ARCHIVE - PowerPoint Presentation for Neknomination
ARCHIVE - PowerPoint Presentation for Neknomination

The aim of this lesson is to help students decide what safeguarding includes and what we are safeguarding against.
The lesson is based around a series of scenarios through which the students will consider if a safeguarding issue is taking place.
-
 Teacher Guide for Safeguarding Lesson
Teacher Guide for Safeguarding Lesson
-
 Class Presentation for Safeguarding Lesson
Class Presentation for Safeguarding Lesson

Cyber bullying is an issue that most young people will be familiar with. In this lesson, students consider the long term implications of cyber bullying. Using scenarios provided, they work in small groups to assess the risks associated with cyber bullying for everyone concerned. They summarise the risks, consequences and likelihood of these consequences for the parties involved and develop posters or display materials for use in the school.

This lesson is all about using Facebook, Twitter and social media networking sites. At the end of the lesson the students will be able to create a poster or display offering social media e-safety advice to other students.
The students are asked to consider the legal implications of the things that are written online by themselves or about themselves online, on social networking sites. Using scenarios, the students have to match the scenarios with the relevant law, and consider the outcomes from a legal perspective.

In this lesson, students are asked to consider how comments made online on social networking sites such as Facebook and Twitter may be perceived by others. It is designed to encourage them to “think before they post” online, and understand how easy it is to write something online that you may end up regretting. During the lesson they consider some quotes that people could post online, and explore how a comment can escalate into full blown cyber bullying.
This is followed by a group exercise with role play to understand how negative comments online develop into conversations. The students then consider how the victim of the bullying would feel, how their family would feel when they saw the comments, and what a stranger might think if they saw the conversation.

Cases have been documented where teachers, young people, parents and even schools have been the victims of impersonation online. In this lesson, students consider what to do if you are being impersonated on Facebook, what to do if you see a Facebook account which you think is impersonating someone you know and how to deal with the effects of being impersonated and seeing someone write unpleasant comments pretending to be you. Students are given a scenario, which they then use as the basis of an investigation into online impersonation, and how you can deal with an imposter account on Facebook. They then create a guide for dealing with impersonation which can be used by other students.

In this lesson, students learn about the risks of “Frape” where someone else uses your Facebook account to send malicious messages, indecent photos or to generally disrupt your online presence. The activity, while focused on Facebook, is helpful in that it is essential that young people understand how and why website security systems work, and how they can make their online behaviour more secure, and take effective steps to keep passwords and logins safe.
The lesson includes a number of relevant links, so having Internet access during the session is recommended.

Sexting, also sometimes called ‘taking selfies’ is an activity which some children consider safe due to a range of incorrect assumptions based on anonymity, depersonalisation, and the abstract, intangible nature of the Internet. None of these assumptions are necessarily true, and the myths should be challenged. If each aspect of the ‘sexting’ behaviour is compared to the same behaviour in ‘public’ or ‘real life’ pupils normally react to the effect that such behaviour would be unsafe or embarrassing in ‘real life’ – this is why it is essential to break down the myths that anonymity provides any layer of safety.
In this lesson, groups of students produce a poster or guide to display advice on what sexting is, how it happens, and how to avoid unsafe situations online, how to deal with the effects of pictures published on the Internet without permission, and how to remove both the images and unpleasant comments caused by the sexting.
The lesson includes practical advice for dealing with sexting, including reporting procedures and the law.

Many young people are unclear about the law relating to file sharing, even in years 9 and 10. This lesson explains exactly what “peer to peer” or “p2p” file sharing is, and which sites are legal. Students learn why p2p networks can be dangerous facilitators of malware and viruses, why p2p networks can facilitate copyright infringement, and how illegal downloads can be traced. An important element of this learning is the understanding of what the potential consequences of illegal downloading can be.
The lesson plan involves a mock trial, where students role play the opposing sides in a case where a student is being prosecuted for illegal file sharing. It also includes useful links for reference, and background information for the teacher.

A digital footprint, also known as a digital shadow, is the trace of a person’s online activity visible on search engines such as Google, social media platforms such as Facebook and Twitter, and image searches such as Google images and Flickr. We all have digital footprints these days, the important thing is to manage them, remembering that the things that we post online, are often difficult to remove.
This lesson reminds students that future employers and universities may search the social media profiles of applicants. The students access the Internet to search online for anything relating to them, to see what their digital footprint is currently like. The pupils develop advice on which websites users need to be wary of and carefully consider what information they upload. They can then develop a series of guidelines aimed at Y7-8 designed to minimise the possibility of negative search results in future.

Certain websites are more likely to foster negative online behaviour than others, and those that encourage Q&A or ratings are often sources of concern for young people who have been targeted with abuse or inappropriate approaches from people they know who are posting anonymously, from people they know who are quite open about their identity or from complete strangers. This lesson shows users how to avoid cyber bullying situations on ratings and response sites, what to be aware of when posting personal comments and the dangers of material being copied across sites and devices.
Using scenarios and role play, students develop strategies for dealing with this kind of cyber bullying and for reporting incidents. The lesson includes opportunities for the students to develop materials for their peers, younger students and the wider school community.

Copyright infringement is common in schools amongst pupils – normally because of ignorance regarding copyright law and the relative ease to find and copy images without considering copyright licenses. Creative Commons is a system of licensing which allows use, reuse, remixing with permission, and legally – provided the user attributes the author in the manner defined in the license. Pupils need to know where to find appropriate content, and how to select material based on a suitable license for their intended use. They also need to be aware of the potential consequences of copyright infringement.
This lesson enables the students to discover how they can use images, information and other media in their own work without breaching copyright rules.

In this lesson students learn how to avoid fraud, phishing, viruses and malware by email. They also learn how to effectively report spam. This is a useful lesson for those students less familiar with email, who may be using it on work placement or in the workplace.
The lesson gives the class an understanding of what spam is and how it works, as well as how to avoid it. Using a number of example emails, the students examine them to see which they think are spam, and why. They then create a display or presentation on the topic for other students, giving their top tips.

Video hijacking, also sometimes called ‘videojacking’ describes a situation where a video has been taken of someone in an embarrassing situation, a situation likely to provoke negative responses, or where a video has been copied, stolen and edited to portray the subject victim in a negative or derogatory light. In this lesson students understand the implications of video hijacking, and the risks of posting video on YouTube. They use real life scenarios to explore the ramifications of the issue, then develop approaches to dealing with it.
The lesson plan also gives them practical strategies for removing video content from YouTube, and asks them to create resources that share their learning with others.

In this lesson students explore different sources of information about sex and relationships and understand the advantages and disadvantages of each. They will be able to define pornography and understand what is, and is not, legal. The lesson helps students understand why people use pornography, issues of consent and respect and dealing with the prevalence of online pornographic content. The lesson includes a quiz, discussion sheet, scenarios and a lengthy PowerPoint presentation to guide teachers through these sensitive issues.

Following on from the previous lesson, this plan continues young people's exploration of the ways in which sources of information about sex can affect values, attitudes and beliefs. The students consider ad campaigns and how they are sold products through sexual imagery and connotation. They are encouraged to focus on how the prevalence of this kind of imagery shapes our beliefs, values and attitudes. The lesson includes two worksheets, useful links and a PowerPoint presentation.

"Sexting" is an increasingly common problem for young people, with pressure to look and behave certain ways from their peers and the media, and a celebrity culture that promotes attention-seeking behaviour. In this lesson, students consider different scenarios involving sexting, and understand the social and legal implications. The lesson includes worksheets, quiz, information sheet and PowerPoint.

Many young people may exhibit inappropriate sexual behaviour, or experience it at the hands of their peers. This lesson plan explores how and why this may happen, and helps young people to deal with it. It considers such behaviour as part of a spectrum, ranging from sexual jokes and bullying through to harassment and sexual exploitation. Students explore the wider social contexts and influences in society and culture. The lesson includes worksheets, role plays for students and a comprehensive PowerPoint presentation.

In this lesson on anti-radicalisation and extremism, students will think about their likes and dislikes in life and who influences their choices.
Students will learn to look at how individuals and groups radicalise others using the Internet. They will understand what is meant by online radicalisation and why people are targeted. They will also learn to be aware of the ‘push’ and ‘pull’ factors related to victims of extremists and know how to support someone who is being targeted by extremists.
-
 Teacher Guide for Online Extremism
Teacher Guide for Online Extremism
-
 Class Presentation for Online Extremism
Class Presentation for Online Extremism

Abuse is a form of maltreatment (in this context, of a child). Somebody may abuse or neglect a child by inflicting harm or by failing to act to prevent harm. Children may be abused in a family or in an institutional or community setting by those known to them or, more rarely, by others (for instance, online). They may be abused by an adult or adults, another child or children.
This short guide defines the different forms of abuse to assist parents in safeguarding their children.

All school and college staff should be aware that abuse, neglect and safeguarding issues are rarely stand-alone events that can be covered by one definition or label. In most cases, multiple issues will overlap with one another.
This checklist is broken down into four sections to help staff identify possible issues. If this checklist raises any concerns about a particular child, it should be discussed with a designated safeguarding lead.

This model policy has been designed to be easily adapted by headteachers and boards of trustees/governing bodies to reflect the ethos of your own school.
The policy includes information on identifying the various forms of abuse. It also provides details on the procedures to be following in the event of an abuse concern.
The policy is on Word format, so it can be adapted to include information specific to your school.
-
 Abuse Policy
Abuse Policy

This useful resource for parents provides key information about alcohol, the law about alcohol and young people and alcoholic units. It also gives advice about why young people experiment with alcohol, ways to prevent underage drinking and tips for parents on how to talk to their child if they have concerns.

This policy is designed as a template for your school to use as a basis for your own school alcohol policy.
The aims of the policy are to ensure that procedures are in place to deal with any incident of alcohol being possessed, consumed or sold on the school site and school trips, to ensure that a comprehensive alcohol education programme is available for all students in school and to ensure that the alcohol education programme is reviewed on a regular basis and that it reflects the values of the school and governors.
The policy is provided in Word format, so it can be modified to suit your own school.
-
 Alcohol Policy
Alcohol Policy

Since 1st July 2015, all schools have a duty under the Counter Terrorism And Security Act to keep children safe from harm, especially from the risks of radicalisation and extremism.
This checklist will help identify the key elements your school should have in place.

Parents should be aware that bullying is taken very seriously at school. However, as a school you cannot monitor pupils around the clock as bullying can occur outside of school.
This guide supports parents in knowing the different types of bullying, signs that their child is being bullied and other agencies that can support them.

The aims of this school policy are to ensure that procedures are in place to deal with bullying in school or off site. It outlines the delivery of anti-bullying lessons as part of the PSHE programme and the promotion of anti-bullying initiatives in school and sets out the sanctions in place for any member of the school community who is involved in bullying.
The policy is provided in Word format so that it can be supplemented with information specific to your school.
-
 Bullying Policy
Bullying Policy

Child sexual exploitation is when a child or young person is in an exploitative situation and receives gifts or other items as a result of performing sexual activities to the abuser. It can also occur through technology when a child or young person is persuaded to post images on the Internet.
It is vital that parents play a role in identifying if their child may be a victim of CSE. This checklist will help them become aware of some of the signs to look out for.

CSE is an important area for all schools to include as part of their safeguarding policy. This checklist is a self-review tool to support the school in ensuring that it has robust policies and procedures in place to deal with any risks associated with CSE.

Parents are naturally worried about their child being exposed to, and potentially experimenting with, drugs. So, this simple guide acts as a checklist for identifying possible signs along with actions that can be taken to discuss this matter with their son/daughter and other agencies.

The Safeguarding Essentials checklist is designed to assist schools when reviewing their drugs education provision.
The checklist is designed as a self-review tool to help identify key provisions for drugs awareness that should be in place as well as actions that the school should take to ensure that policies, training and lesson delivery is up to date.

This policy is designed as a template for your school to use as a basis for your own school alcohol policy.
This policy applies to pupils, staff, parents/carers and visitors. It applies on the school site, and also applies to pupils and staff when off-site. This includes when the staff are acting in loco parentis, for example during school visits or residentials.
The policy also affects the use of school premises after normal school hours. Organisers of any after-school events should be made aware of the policy and their responsibility to implement it.
The policy is provided in Word format, so it can be modified to suit your own school.
-
 Drugs Policy
Drugs Policy

This factsheet gives parents a general overview of e-safety. Schools can email it to parents, hand it out at parents evening or incorporate it into your newsletter to help raise awareness of e-safety issues for children and how these affect parents. It gives parents an overview of the positive and negative aspects of the Internet, some key statistics, tips and useful links.

This policy supports the PREVENT duty for schools as part of the Counter Terrorism and Security Act (2015).
The policy should be used as part of the overall safeguarding policy and it supports and complements the ‘British Values set out in the Department of Education guidance, ‘Promoting fundamental British values as part of SMSC in schools’
The policy is provided in Word format, so it can be modified to suit your own school.

Teachers in England and Wales have a mandatory duty to report known cases of FGM in girls under 18 years old to the police. The FGM duty came into force on 31 October 2015. It is important that parents know that if they have any concerns regarding FGM relating to a child in school, they can speak to the DSL who will advise and act as appropriate.
This guide provides some key information for parents about the types of FGM, the law and health implications.

Female Genital Mutilation is an illegal act. However, around 60,000 girls are thought to currently be at risk of the procedure in the UK.
This checklist for schools and staff provides a quick guide to signs that could suggest that a girl is at risk of undergoing the procedure. It also offers indicators that may demonstrate that FGM has taken place.

This template policy sets out the actions the school will undertake to protect students and ensure that they are informed about FGM.
This policy also acts as a guide for staff in understanding how to spot signs of FGM in order to protect pupils.
This resource is provided in Microsoft Word to allow it to be adapted and made specific to your school.
-
 FGM Policy
FGM Policy

The role which the school governor plays in not only developing, but also implementing an e-safety strategy in school is vital.
The Department for Education have highlighted a number of key features of effective practice in relation to online safety in schools and Ofsted have placed greater emphasis on inspecting the effectiveness of the governing body in ensuring that schools meet all of these criteria.
This checklist can be used by school governors as a starting point for assessing the provision in your school.

This resource sheet supports the KSCIE online training course and provides links to further information across a range of safeguarding topics.
-
 Keeping Children Safe in Education Resource Sheet
Keeping Children Safe in Education Resource Sheet

It is important for parents to ensure that they can support the mental well-being of their children, as they would for any physical condition.
This mental well-being guide for parents will help them to identify signs of mental health problems, factors which could lead to future problems and strategies to promote positive mental well-being.

The mental well-being policy focuses on the well-being of pupils, however, recognition is also given to the importance of the well-being of staff.
This policy is designed as a template for your school to use as a basis for your own school mental well-being policy and is provided in Word format, so it can be modified to suit your own school.
The policy aims to ensure that the school promotes mental well-being and all students have the right to access services if they need further support.
-
 Mental Well-being Policy
Mental Well-being Policy

Parents may have heard the phrase ‘safeguarding’ before and wondered what it meant.
This guide for parents introduces the term 'safeguarding' and goes on to explain their role in keeping their children safe from abuse and maltreatment, preventing harm to their health and development and providing safe and effective care for them.

This model policy has been designed to be easily adapted by headteachers and boards of trustees/governing bodies to help develop a comprehensive safeguarding policy your own school.
The Safeguarding Policy has various links with the wider Safeguarding agenda and staff and trustees/governors should always be aware of the impact this policy has on other, related issues. These links are outlined within the policy document.
-
 Safeguarding Policy
Safeguarding Policy

This handy guide that schools can share with parents provides some key information about sexting (or Youth Produced Sexual Imagery).
The parent guide includes information regarding attitudes to sexting, the law and potential consequences of taking and sharing inappropriate images, tips on what parents can do and links to useful websites.

School leaders can use the sexting checklist when reviewing their strategies in dealing with incidents of children and young people creating, sharing and possessing indecent images (sometimes known as Youth Produced Sexual Imagery).
It is important that schools regularly use this checklist to ensure that policies, training and lesson delivery is up to date.

The policy is provided in Word format, so it can be modified to suit your own school.
This sexting policy for schools aims to ensure that the school has procedures in place to deal with any sexting incident in school and/or the local community if pupils’ welfare is at risk. It also provides information for staff on how to search, confiscate and remove any inappropriate or indecent image a pupil may have on their mobile device. Overall, the policy is designed to ensure resilience for the school in light of any sexting incident including ways to support students and parents/carers.
-
 Sexting Policy
Sexting Policy

The internet brings marvellous opportunities to children and young people with the ability to learn new skills and visit websites which engage and enrich their lives. However, the internet also brings dangers such as online predators who will try and contact children through websites and software applications.
This guide will help parents and carers learn more about the danger of their children being targeted by online extremists. The guide provides information to help them identify the issue of online radicalisation and gives suggestions on how to support their children with the threat of online extremism.
- Safeguarding & E-Safety:
- Online Checklist
- Guidance Documents
- Support and Advice
- News & Information Widget
Get started with free safeguarding and e-safety guidance and articles in our regular email updates and special reports.
Join as a E-safety Support member for access to Internet safety specific online training modules for staff, governors, pupils and parents, school e-safety policies, lesson plans and teaching resources.
Join our full Safeguarding Essentials service for all the fantastic e-safety resources, plus more online training, classroom resources, policies and parent guides covering the wider safeguarding topics.
Discounts available for school groups, small schools and special needs schools - please call 0113 526 5980
* All prices are shown excluding VAT. This is a subscription product with an automatic annual renewal.
Renewal can be cancelled at any time up until midnight on the last day of the current subscription.




